Researchers stated they just lately found a zero-day vulnerability within the 7-Zip archiving utility that was actively exploited as a part of Russia’s ongoing invasion of Ukraine.
The vulnerability allowed a Russian cybercrime group to override a Home windows safety designed to restrict the execution of recordsdata downloaded from the Web. The protection is usually referred to as MotW, quick for Mark of the Internet. It really works by inserting a “Zone.Identifier” tag on all recordsdata downloaded from the Web or from a networked share. This tag, a sort of NTFS Alternate Knowledge Stream and within the type of a ZoneID=3, topics the file to further scrutiny from Home windows Defender SmartScreen and restrictions on how or when it may be executed.
There’s an archive in my archive
The 7-Zip vulnerability allowed the Russian cybercrime group to bypass these protections. Exploits labored by embedding an executable file inside an archive after which embedding the archive into one other archive. Whereas the outer archive carried the MotW tag, the inside one didn’t. The vulnerability, tracked as CVE-2025-0411, was mounted with the discharge of model 24.09 in late November.
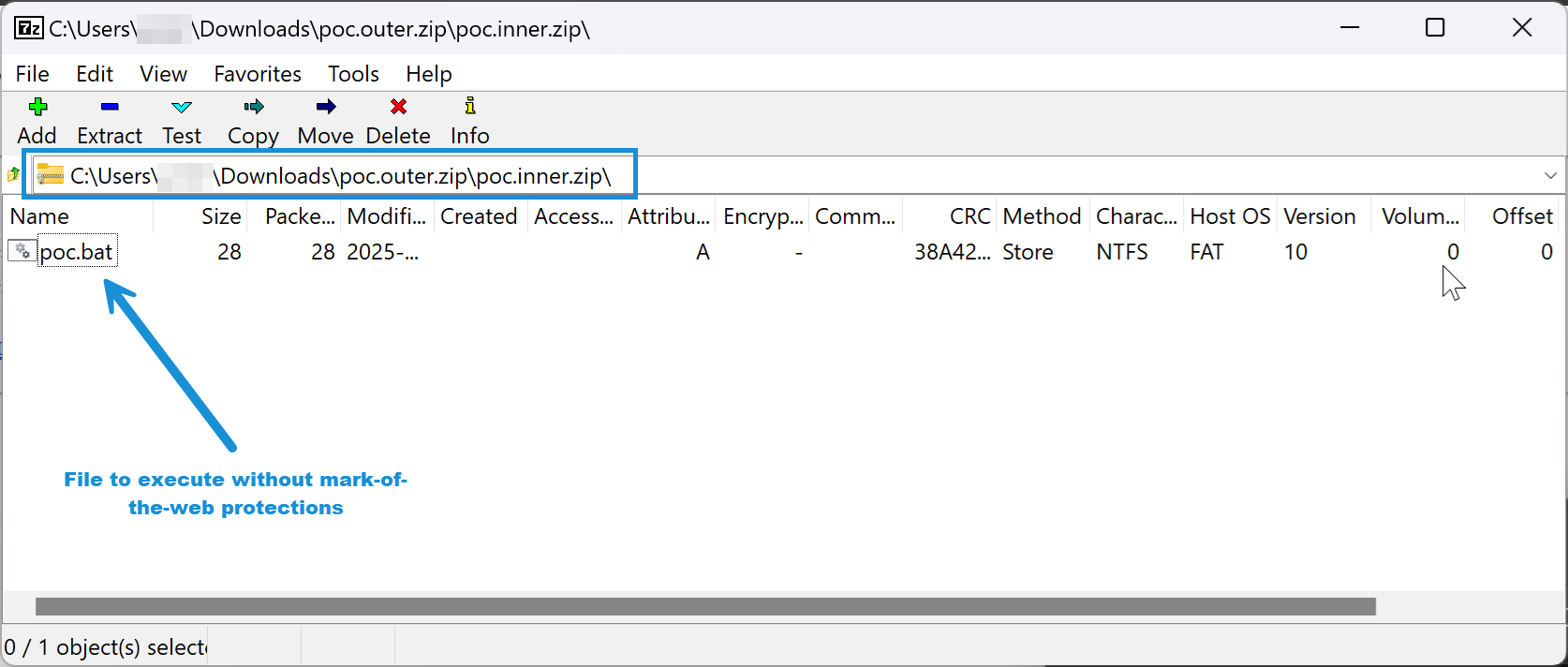
Tag attributes of outer archive exhibiting the MotW.
Credit score:
Development Micro
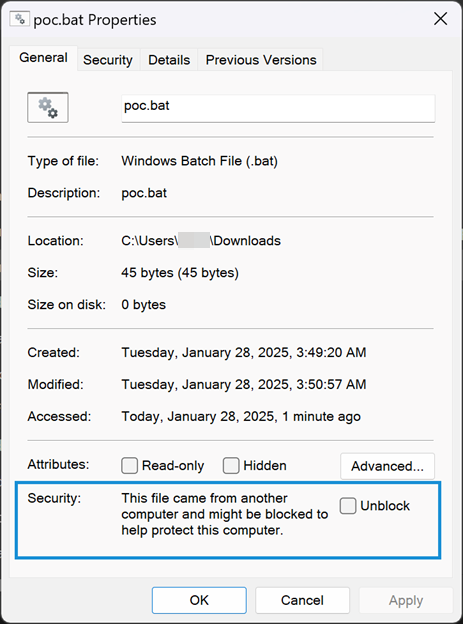
Attributes of inner-archive exhibiting MotW tag is lacking.
Credit score:
Development Micro
“The foundation reason for CVE-2025-0411 is that previous to model 24.09, 7-Zip didn’t correctly propagate MoTW protections to the content material of double-encapsulated archives,” wrote Peter Girnus, a researcher at Development Micro, the safety agency that found the vulnerability. “This enables risk actors to craft archives containing malicious scripts or executables that won’t obtain MoTW protections, leaving Home windows customers susceptible to assaults.”


